How Software is Crucial to Your EV Security
EV Security: Why It Matters
Improper data security management can be absolutely detrimental to an organisation.
GDPR breaches are no laughing matter, with companies like Meta being hit with fines as high as $1.2bn in failing to comply with regulations in their transfer of personal data from the EU to US. And beyond data handling - general network security is something of huge importance to any organisation in the digital age, with EV charging being no exception.
Take the well-worn example back in April of last year with charge points in the Isle of Wight. Hackers were able to take advantage of display screens and play explicit content from a third-party site, causing an incident that was covered across the world’s media.
This may be an extreme example of the extent of the damage bad actors can do to unprepared systems, but it highlights the potential for breaches as EV adoption grows and the need for a larger charging infrastructure rises.
At Clenergy EV, we know that the charging infrastructure in the UK needs improving. Industry surveys have frequently cited huge numbers of EV drivers praising their cars (as high as 94% according to some research), but frustration in the current public charging infrastructure.
And while placing more chargers in the ground is an essential part of solving these issues, it will mean little if they’re not backed with a solid and robust network that allows fair, easy, and most of all, secure use across chargers.
That’s where we believe software can make all the difference.
In this blog, we’ll cover what you need to look for from a security standpoint when partnering with back-office software.
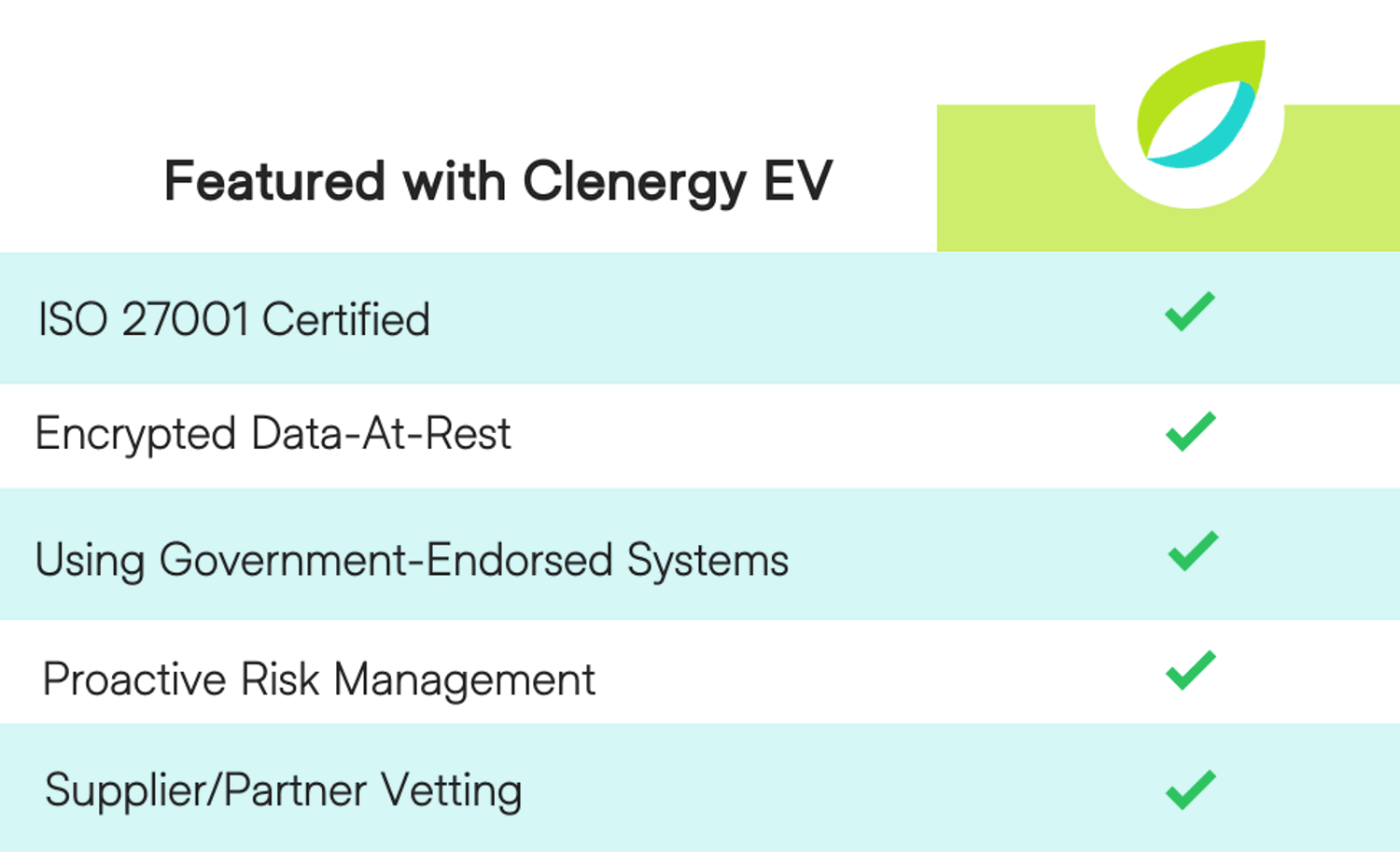
What to look for from your EV Charging provider
ISO 27001: ISO 27001 is the leading international standard on information security. Its framework requires organisations to identify information security risks and select appropriate controls to tackle them.
It’s not just another acronym to add to our name. ISO certification tells you that our processes for handling information are approved by international standards - so you don’t just have to take our word for it.
Encrypted data-at-rest: Of course, encryption is the act of coding information so that it’s unintelligible to the average viewer. Encryption involves a method of scrambling and unscrambling information, usually during end-to-end data transfers to ensure it can’t be intercepted and pried upon.
In our case, however, we take no chances in making sure your data is secure, and make sure to encrypt the data we process even when it’s at rest.
Using government-backed systems: Our cyber-essentials certification means we’re again stamped with an international standard for security. The certification is endorsed by the UK government (NCSC), and sits as part of our wider commitment to putting security first.
Proactive Risk Management: In case of trouble, we have a clear plan to address it swiftly.
But the way we view it is that by putting preventative measures in place, we negate the need for such a response. To action this, we employ complete surveillance of our network, craft our internal policies using GDPR and UK regulations as a key informer, and insure all of our employees are trained to handle your data securely.
Supplier/Partner Vetting: We understand that a laissez-faire attitude to security is not an option.
We vet third-party clients and suppliers to ensure their security policies are in line with ours, to prevent any data mishandling.
Why do we do it?
The EV revolution is here. Despite the government’s move to push back the ban on ICE car sales to 2035, zero-emission vehicles are still mandated to account for 80% of all new car sales by 2030. With this massive influx in uptake coming, we need to make sure our infrastructure systems are prepared. And in using software to aid that, we are certain that they will be.
Aside from being essential in creating the fair and open charging network we so often champion, we also need to have security systems such as those discussed in this article in place to make sure that public confidence is maintained.
And we believe that’s just as important for residential users as it is for drivers within a larger fleet.
With Clenergy EV, we offer you the chance to be proactive about your organisation’s security, partnering with a proven and reliable software provider to make sure your network isn’t affected, taking one more thing off your mind during your EV transition.
To learn more about what our software has helped clients like Nottingham City Council achieve, click through to some of our other blogs on the subject, or simply contact us via the credentials below.